API security refers to the methods and tools designed to protect the API and mitigate cyber attacks that attempt to access and destroy sensitive data and disrupt services. The security of APIs is critical in today's digital age to protect sensitive data, prevent data breaches, secure mobile applications, maintain trust with users, and maintain business continuity.
APIs have become very important because enable development efficiency in modern software development hence the growing reliance on API. They are responsible for integration, implementation, and data exchange between software systems, accelerating business growth.
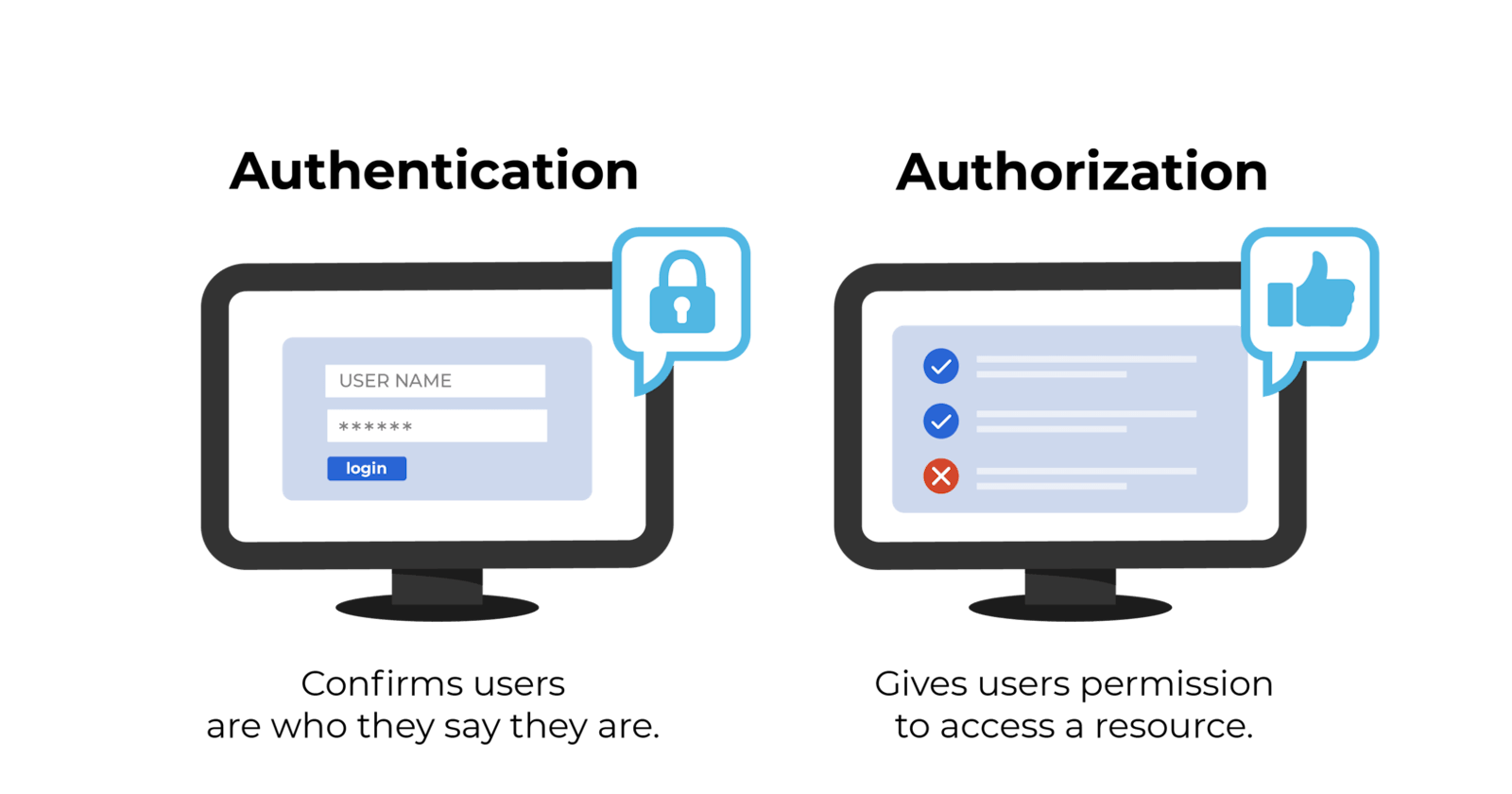
This article aims to highlight the best practices for authentication and authorization as well as their importance to API security. Authentication is the process of verifying the identity of the user or application interacting with the API to prevent cyberattacks. At the same time, Authorization is verifying what the user has access to based on their roles and privileges controlling access to sensitive data. They are both essential for protecting sensitive data and preventing unauthorized access or activities.
Authentication Best Practices
Some authentication practices are known widely, practices such as;
Implementing strong password policies that encourage users to create strong, complex passwords.
Implementing multi-factor authentication(MFA) by combining something like a password with biometric data or a code is sent.
Session management, using secure, random session IDs and regenerating session IDs after login
Implementing account lockout policies, temporary locking accounts after several unsuccessful attempts to log in
Education of users about the importance of strong authentication practices and encouraging them to report suspicious activities.
Other lesser-known methods of authentication are;
Token-based Authentication: This is an authentication method that uses tokens generated to authenticate users. After successful authentication, a token usually containing user ID and roles is generated by the authentication servers. The token is issued to the client who then stores it, for every request the client makes to access a protected resource, the token has to be included in the request header. The client gains access to the requested resource if the token is valid and the client has required permission.
The main types of tokens that are used are JWT(JSON Web Token) and OAuth 2.0, they can be used in combination with each other or individually. Token-based authentication provides scalability, statelessness, security, and also flexibility.
API Keys: They are unique identifiers provided by API providers used to track and control the usage of APIs, they are used to authenticate and authorize access to API. API keys like tokens can also be included in the request header when making an API request or sometimes in the request body.
API keys have to be treated like sensitive information and kept secure to prevent unauthorized access by rotating the API keys to minimize the risk of unauthorized access, implementing expiration date for the API keys, monitoring and auditing API key usage regularly, and permission restriction by granting permissions for specific functionalities or resources needed to be accessed.

Authorization Best Practices
Some general authorization practices are using strong, complex passwords, implementing multi-factor authentication, and limiting permissions to minimize the risk of compromise.
Other authorization practices are;
Role-Based Access Control (RBAC): RBAC is an access control model that uses roles instead of user identity to grant access. Access rights are granted based on job responsibilities, ensuring that users only have the necessary privileges to perform job functions.
Some RBAC implementations support hierarchical roles, allowing for more slight access control for higher roles to encompass the permissions of lower-level roles, there should be regular auditing and monitoring of user activity to detect and respond to any suspicious activity, and also users and administrators should be educated about the RBAC model, its benefits, and how it affects access controls. RBAC simplifies access management, enhances security, and contributes to a more efficient and scalable approach to access control.
Scope-based access: Scope-based access control is an access control model that grants or restricts access to resources based on predefined scopes. Scope refers to a specific set of permissions or actions that a user or application is allowed to perform, They specify what actions or data the application is allowed to access.
Access is usually granted by issuing an access token containing information about the granted scope and is verified by the resource server upon request. Regular auditing and monitoring are also done to track scope usage to identify unauthorized scope usage, tokens should be revoked in case of compromised tokens, and the resource server should validate access tokens and enforce the granted scopes. By defining and managing scopes effectively, organizations can implement a flexible and granular access control mechanism that aligns with their specific security and privacy requirements.

Conclusion
All though, authentication and authorization may sound alike, they each play a different role in securing systems and data. Unfortunately, people often use both terms interchangeably as they both refer to system access. However, they are distinct processes. Simply put, authentication verifies the identity of a user or service before granting them access, while authorization determines what they can do once they have access. They are also similar in the way they both leverage identity. For example, authentication verifies an identity before granting access, while authorization uses this verified identity to control access.